Similar Posts

The Total Economic Impact™ Of Microsoft Entra
Maintaining your identity and access management (IAM) solution shouldn’t strain your budget. @Microsoft Entra can save you money and generate ROI. Get the Forrester report on the total economic impact of Entra with data from Microsoft customers.
@Microsoft Security

Sycomp Storage: Innovates AI for Healthcare with Migration of HPC Environment to Azure
Transform healthcare with Azure’s high-performance computing. Sycomp Storage redefines data management, enabling fast, scalable solutions for #AI and #ML workloads. Explore the benefits & why it matters for your business growth. Learn More 👇 #Azure #HPC #Innovation
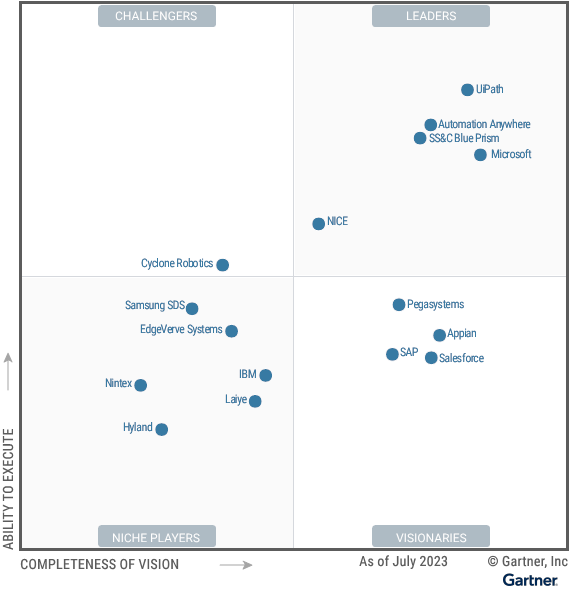
Gartner Magic Quadrant for Robotic Process Automation
It’s clear that flexible work is here to stay and technological investments will continue to be a major priority for organizations looking to advance past their competition. Read this @Microsoft 365 blog that highlights how Microsoft has been recognized as a Leader in the 2023 Gartner® Magic Quadrant™ for Desktop as a Service, and how organizations are using Windows 365 and Azure Virtual Desktop to deliver better productivity and collaboration.

How to Discover, Assess, Migrate and Modernize with Azure Migrate
Looking for guidance on your move to the #cloud? See how the @Microsoft #Azure Migrate service tracks migration progress using a central dashboard that provides intelligent insights along the journey. Watch the video and contact a Microsoft Azure Migrate expert at Mowry International for next steps.
@Azure Virtual Desktop

Identity-Centric Threats: The New Reality
The way cybercriminals operate has fundamentally changed. The eSentire’s 2025 Identity Threat Research Report, “Identity-Centric Threats: The New Reality” reveals how identity-based attacks have surged 156% since 2023, now representing nearly 60% of all confirmed threat cases.
Powered by Cybercrime-as-a-Service models, these attacks leverage Phishing-as-a-Service platforms like Tycoon2FA to bypass multi-factor authentication and gain rapid access to business email accounts and sensitive data.
Download your complimentary copy of the report for expert insight on:
-Rapid evolution of phishing and infostealer malware that turn stolen credentials into profitable identity marketplaces
-Exploitation of unmonitored endpoints and shadow IT for ransomware deployment
-Strategic recommendations for building a Zero Trust identity architecture and implementing phish-resistant authentication
DM me to discover how Mowry International can help you reduce your exposure to ident
Canopius enables data & AI innovation by building a strong foundation with Azure
Does your IT infrastructure have the scalability, agility, and elasticity to handle modern data requirements? If it’s impeding data access, read this customer story about how insurance giant Canopius shifted from the complications of dual data centers to the geographically scalable and cost-effective cloud environment in @Microsoft Azure.